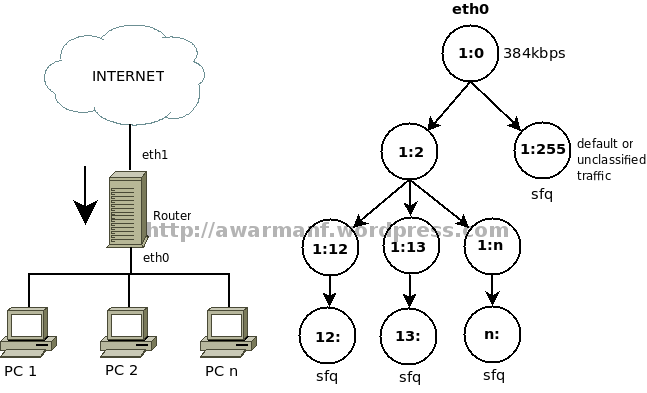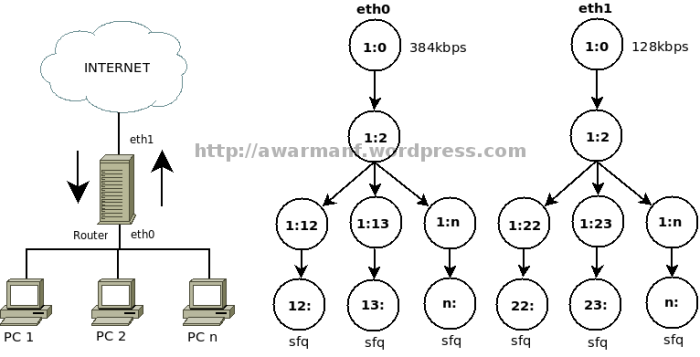
Kriteria dalam pembuatan traffic control ini:
- Traffic control hanya untuk trafik eggress dari device lan (eth0) dan wan (eth1).
- Trafik dari local area network (lan) ke router dan sebaliknya tidak melalui traffic control.
- Trafik dari internet ke lan (downstream) akan melalui traffic control, kecuali trafik dari port 80 (www) yang mempunyai tanda TOS 0×30 atau DSCP 12 (cache hit).
- Setiap pc atau anggota lan akan memiliki class dan qdisc sendiri-sendiri.
- Tidak ada class default untuk handle traffic untuk object yang tidak didefinisikan atau unclassified traffic.
Topologi network
Network LAN : 192.168.41.0/24 IP Router : 192.168.41.1 IP Client : 192.168.41.2 - 192.168.41.14 Device LAN : eth0 Device WAN : eth1
Alokasi bandwidth internet downstream
Root - Ceiling : 384kbps - Rate : 384kbps Client - Ceiling : 384kbps - Rate : 16kbps
Alokasi bandwidth internet upstream
Root - Ceiling : 128kbps - Rate : 128kbps Client - Ceiling : 128kbps - Rate : 16kbps
Source Code tc-3.sh
001 | #!/bin/sh |
002 |
003 | # File: tc-3.sh |
004 | # |
005 | # Deskripsi: Trafik control untuk membatasi downstream dan upstream dengan htb |
006 | # |
007 | # Kriteria: |
008 | # 1. Traffic control hanya untuk trafik eggress dari device lan (eth0) dan wan (eth1). |
009 | # 2. Trafik dari local area network (lan) ke router dan sebaliknya tidak melalui traffic control. |
010 | # 3. Trafik dari internet ke lan atau downstream akan melalui traffic control, kecuali trafik |
011 | # dari port 80 (www) yang mempunyai tanda TOS 0×30 atau DSCP 12 (cache hit). |
012 | # 4. Setiap pc atau anggota lan akan memiliki class dan qdisc sendiri-sendiri. |
013 | # 5. Tidak ada class default untuk handle traffic untuk object yang tidak didefinisikan atau unclassified traffic. |
014 | # |
015 | # Created by Arief Yudhawarman (2009) |
016 | # Email: awarmanff at yahoo.com |
017 | # |
018 |
019 | IPTABLES="/usr/sbin/iptables" |
020 | TC="/sbin/tc" |
021 |
022 | # parameter |
023 | LAN="eth0" |
024 | WAN="eth1" |
025 |
026 | # Bandwidth |
027 | # (kbps) |
028 | # ROOT CLASS |
029 | # Downstream |
030 | RATEDW=384 |
031 | CEILDW=384 |
032 | # Upstream |
033 | RATEUP=128 |
034 | CEILUP=128 |
035 | # |
036 | # SUB CLASS |
037 | # Downstream |
038 | RATESUBDW=16 |
039 | CEILSUBDW=384 |
040 | # Upstream |
041 | RATESUBUP=16 |
042 | CEILSUBUP=128 |
043 |
044 | # parameter |
045 | LAN="eth0" |
046 | WAN="eth1" |
047 |
048 | # |
049 | # IPTABLES |
050 | # PACKET MANGLE |
051 | # |
052 |
053 | # |
054 | # FLUSH table |
055 | # |
056 | $IPTABLES -F -t mangle |
057 |
058 | # |
059 | # PREROUTING |
060 | # |
061 | # Incoming traffic to WAN |
062 | # |
063 | # packets cache hit with dscp 12 (tos 30) set mark to 5 |
064 | iptables -A PREROUTING -t mangle -i $WAN -p tcp --sport 80 -m dscp --dscp 12 -j MARK --set-mark 5 |
065 | iptables -A PREROUTING -t mangle -i $WAN -p tcp --sport 80 -m dscp --dscp 12 -j RETURN |
066 | # others set mark to 6 |
067 | iptables -A PREROUTING -t mangle -i $WAN -j MARK --set-mark 6 |
068 | # |
069 | # Incoming traffic to LAN |
070 | # |
071 | # mark packets to 7 |
072 | iptables -A PREROUTING -t mangle -i $LAN -j MARK --set-mark 7 |
073 |
074 | # |
075 | # FORWARD |
076 | # |
077 | # Incoming traffic from outside (wan) forwarded to inside (lan) |
078 | # |
079 | # catch cache hit with fwmark 5 and set mark to 0x212 |
080 | iptables -A FORWARD -t mangle -p tcp -m mark --mark 5 -j MARK --set-mark 0x212 |
081 | # |
082 | # mark packets based on destination ip |
083 | for i in `seq 2 14` |
084 | do |
085 | j=$((i+10)) |
086 | iptables -A FORWARD -t mangle -d 192.168.41.$i -m mark --mark 6 -j MARK --set-mark $j |
087 | done |
088 | # |
089 | # Incoming traffic from inside (lan) forwarded to outside (wan) |
090 | # |
091 | # catch fwmark 7 and set mark according to source ip |
092 | for i in `seq 2 14` |
093 | do |
094 | j=$((i+20)) |
095 | iptables -A FORWARD -t mangle -s 192.168.41.$i -m mark --mark 7 -j MARK --set-mark $j |
096 | done |
097 |
098 | # |
099 | # TRAFFIC CONTROL |
100 | # |
101 |
102 | # |
103 | # DOWNSTREAM |
104 | # |
105 | # Create qdisc & class |
106 | tc qdisc del dev $LAN root |
107 | tc qdisc add dev $LAN root handle 1:0 htb |
108 | tc class add dev $LAN parent 1:0 classid 1:2 htb rate ${RATEDW}kbit ceil ${CEILDW}kbit quantum 1500 prio 6 |
109 |
110 | # |
111 | # Sub class of parent 1:2 |
112 | # |
113 | # IP Clients 192.168.41.2 - 192.168.41.14 |
114 | for i in `seq 2 14` |
115 | do |
116 | j=$((i+10)) |
117 | # create class per ip address |
118 | tc class add dev $LAN parent 1:2 classid 1:$j htb rate ${RATESUBDW}kbit \ |
119 | ceil ${CEILSUBDW}kbit quantum 1500 prio 6 |
120 | # attach qdisc |
121 | tc qdisc add dev $LAN parent 1:$j handle $j sfq perturb 10 |
122 | done |
123 |
124 | # |
125 | # Filter traffic |
126 | # |
127 | # IP Clients 192.168.41.2 - 192.168.41.14 |
128 | for i in `seq 2 14` |
129 | do |
130 | j=$((i+10)) |
131 | # Attach filter to flowid with specified handle (packet mark) |
132 | tc filter add dev $LAN protocol ip parent 1:0 prio 6 handle $j fw flowid 1:$j |
133 | done |
134 |
135 | # |
136 | # UPSTREAM |
137 | # |
138 | # Create qdisc & class |
139 | tc qdisc del dev $WAN root |
140 | tc qdisc add dev $WAN root handle 1:0 htb |
141 | tc class add dev $WAN parent 1:0 classid 1:2 htb rate ${RATEUP}kbit ceil ${CEILUP}kbit quantum 1500 prio 6 |
142 |
143 | # |
144 | # Sub class of parent 1:2 |
145 | # |
146 | # IP Clients 192.168.41.2 - 192.168.41.14 |
147 | for i in `seq 2 14` |
148 | do |
149 | j=$((i+20)) |
150 | # create class per ip address |
151 | tc class add dev $WAN parent 1:2 classid 1:$j htb rate ${RATESUBUP}kbit \ |
152 | ceil ${CEILSUBUP}kbit quantum 1500 prio 6 |
153 | # attach qdisc |
154 | tc qdisc add dev $WAN parent 1:$j handle $j sfq perturb 10 |
155 | done |
156 |
157 | # |
158 | # Filter traffic |
159 | # |
160 | # IP Clients 192.168.41.2 - 192.168.41.14 |
161 | for i in `seq 2 14` |
162 | do |
163 | j=$((i+20)) |
164 | # Attach filter to flowid with specified handle (packet mark) |
165 | tc filter add dev $WAN protocol ip parent 1:0 prio 6 handle $j fw flowid 1:$j |
166 | done |
Sumber: Manual mikrotik refman2.9.pdf.
Analisa paket mangle dan traffic control untuk trafik downstream
Perhatikan baris-baris yang tercetak tebal.
- tc -s -d qdisc show dev eth0; iptables -L FORWARD -t mangle -nv| head -n 16
qdisc htb 1: r2q 10 default 0 direct_packets_stat 6144 ver 3.17
Sent 31783127 bytes 49709 pkts (dropped 0, overlimits 5839)
qdisc sfq 12: parent 1:12 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 5118517 bytes 15858 pkts (dropped 0, overlimits 0)
qdisc sfq 13: parent 1:13 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 81859 bytes 206 pkts (dropped 0, overlimits 0)
qdisc sfq 14: parent 1:14 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 6626893 bytes 6817 pkts (dropped 0, overlimits 0)
qdisc sfq 15: parent 1:15 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 16: parent 1:16 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 17: parent 1:17 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 11525 bytes 45 pkts (dropped 0, overlimits 0)
qdisc sfq 18: parent 1:18 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 8475558 bytes 11965 pkts (dropped 0, overlimits 0)
qdisc sfq 19: parent 1:19 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 3277886 bytes 4621 pkts (dropped 0, overlimits 0)
qdisc sfq 20: parent 1:20 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 21: parent 1:21 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 4558 bytes 23 pkts (dropped 0, overlimits 0)
qdisc sfq 22: parent 1:22 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 23: parent 1:23 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 24: parent 1:24 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 3012356 bytes 4030 pkts (dropped 0, overlimits 0)
Chain FORWARD (policy ACCEPT 1676K packets, 904M bytes)
pkts bytes target prot opt in out source destination
4921 4911K MARK tcp -- * * 0.0.0.0/0 0.0.0.0/0 MARK match 0x5 MARK set 0x212
15858 4897K MARK all -- * * 0.0.0.0/0 192.168.41.2 MARK match 0x6 MARK set 0xc
206 78975 MARK all -- * * 0.0.0.0/0 192.168.41.3 MARK match 0x6 MARK set 0xd
6817 6531K MARK all -- * * 0.0.0.0/0 192.168.41.4 MARK match 0x6 MARK set 0xe
0 0 MARK all -- * * 0.0.0.0/0 192.168.41.5 MARK match 0x6 MARK set 0xf
0 0 MARK all -- * * 0.0.0.0/0 192.168.41.6 MARK match 0x6 MARK set 0x10
45 10895 MARK all -- * * 0.0.0.0/0 192.168.41.7 MARK match 0x6 MARK set 0x11
11966 8308K MARK all -- * * 0.0.0.0/0 192.168.41.8 MARK match 0x6 MARK set 0x12
4621 3213K MARK all -- * * 0.0.0.0/0 192.168.41.9 MARK match 0x6 MARK set 0x13
0 0 MARK all -- * * 0.0.0.0/0 192.168.41.10 MARK match 0x6 MARK set 0x14
23 4236 MARK all -- * * 0.0.0.0/0 192.168.41.11 MARK match 0x6 MARK set 0x15
0 0 MARK all -- * * 0.0.0.0/0 192.168.41.12 MARK match 0x6 MARK set 0x16
0 0 MARK all -- * * 0.0.0.0/0 192.168.41.13 MARK match 0x6 MARK set 0x17
4030 2956K MARK all -- * * 0.0.0.0/0 192.168.41.14 MARK match 0x6 MARK set 0x18Analisa paket mangle dan traffic control untuk trafik upstream
Perhatikan baris-baris yang tercetak tebal.
- tc -s -d qdisc show dev eth1; iptables -L FORWARD -t mangle -nv
qdisc htb 1: r2q 10 default 0 direct_packets_stat 191743 ver 3.17
Sent 45055014 bytes 244485 pkts (dropped 0, overlimits 4314)
qdisc sfq 22: parent 1:22 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 3539507 bytes 16353 pkts (dropped 0, overlimits 0)
qdisc sfq 23: parent 1:23 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 55439 bytes 324 pkts (dropped 0, overlimits 0)
qdisc sfq 24: parent 1:24 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 1213280 bytes 6968 pkts (dropped 0, overlimits 0)
qdisc sfq 25: parent 1:25 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 26: parent 1:26 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 27: parent 1:27 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 9806 bytes 56 pkts (dropped 0, overlimits 0)
qdisc sfq 28: parent 1:28 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 2949492 bytes 15990 pkts (dropped 0, overlimits 0)
qdisc sfq 29: parent 1:29 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 1039116 bytes 6678 pkts (dropped 0, overlimits 0)
qdisc sfq 30: parent 1:30 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 31: parent 1:31 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 5156 bytes 39 pkts (dropped 0, overlimits 0)
qdisc sfq 32: parent 1:32 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 33: parent 1:33 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 0 bytes 0 pkts (dropped 0, overlimits 0)
qdisc sfq 34: parent 1:34 limit 128p quantum 1514b flows 128/1024 perturb 10sec
Sent 1071110 bytes 6334 pkts (dropped 0, overlimits 0)
Chain FORWARD (policy ACCEPT 1693K packets, 912M bytes)
pkts bytes target prot opt in out source destination
......
16471 3316K MARK all -- * * 192.168.41.2 0.0.0.0/0 MARK match 0x7 MARK set 0x16
331 51239 MARK all -- * * 192.168.41.3 0.0.0.0/0 MARK match 0x7 MARK set 0x17
7154 1125K MARK all -- * * 192.168.41.4 0.0.0.0/0 MARK match 0x7 MARK set 0x18
0 0 MARK all -- * * 192.168.41.5 0.0.0.0/0 MARK match 0x7 MARK set 0x19
1 40 MARK all -- * * 192.168.41.6 0.0.0.0/0 MARK match 0x7 MARK set 0x1a
56 9022 MARK all -- * * 192.168.41.7 0.0.0.0/0 MARK match 0x7 MARK set 0x1b
17496 2811K MARK all -- * * 192.168.41.8 0.0.0.0/0 MARK match 0x7 MARK set 0x1c
7498 986K MARK all -- * * 192.168.41.9 0.0.0.0/0 MARK match 0x7 MARK set 0x1d
0 0 MARK all -- * * 192.168.41.10 0.0.0.0/0 MARK match 0x7 MARK set 0x1e
39 4610 MARK all -- * * 192.168.41.11 0.0.0.0/0 MARK match 0x7 MARK set 0x1f
0 0 MARK all -- * * 192.168.41.12 0.0.0.0/0 MARK match 0x7 MARK set 0x20
0 0 MARK all -- * * 192.168.41.13 0.0.0.0/0 MARK match 0x7 MARK set 0x21
6913 1019K MARK all -- * * 192.168.41.14 0.0.0.0/0 MARK match 0x7 MARK set 0x22Hal yang menarik di sini adalah
- Semua paket yang lewat chain FORWARD table mangle dengan tujuan lan mempunyai jumlah paket yang sama dengan yang tercatat di qdisc dev eth0 (lan).
- Semua paket yang lewat chain FORWARD table mangle dengan tujuan wan mempunyai jumlah paket yang senantiasa sama atau lebih besar dengan yang tercatat di qdisc dev eth1 (wan). Hal ini karena ada beberapa paket yang di-DROP di chain FORWARD table default. Terlihat pada gambar trafik flow di atas, setelah paket melewati chain FORWARD table mangle selanjutnya akan masuk chain FORWARD table filter.
- Jika ingin membatasi trafik upstream dari lan tanpa melewati chain FORWARD, maka ini bisa dilakukan di chain PREROUTING table mangle.